 A hacker by the handle of Barbaros-DZ from Algeria has hacked and deface 32 Chinese government websites.
A hacker by the handle of Barbaros-DZ from Algeria has hacked and deface 32 Chinese government websites. The hacker contacted us about his latest hack in which he defaced 32 important Chinese government owned websites, the hacker left his deface page and a message on all the hacked websites but reason for hacking the sites was not mentioned.
ccording to the message:
Hacked by Barbaros-DZ Algerian HackerThe targeted websites belong to high profile and decision making authorities in China, for example:
Greetz: Bb0yH4cK3r_Dz | BOB_Dz | Dz Mafia | HTC 28 DZ | Kader11000
Ked Ans | Smail002 | TiGER-M@TE | The-DarKKn!ght | x00t | yasMouh
www.dz4all.com | www.dz-mafia.net | www.elkadimoun.org | www.htc28dz.net | www.htc-hacker.com
Contact: barbaros “@” live.ru
To be continued…
The website of Organization Department of the Communist Party of China Central Committee , a department of the Secretariat of the Communist Party of China Central Committee that controls staffing positions within the CPC.
zyz.ajdj.gov.cn
Mirror of the hacked website:
http://www.zone-h.org/mirror/id/18775446
The website of China’s Jingde County Standing Committee
jdxrdcwh.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18780729
The website of Jurong Police Information Network
jrga.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18779719
The website of Jiawang District, People’s Government Information Network Center
http://w08.xzjw.gov.cn/
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18776093
The website of Jiaozuo City Office of Emergency Management
yjglbgs.jiaozuo.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18776703
The website of Yancheng District Department of Transportation
jtj.lhyc.gov.cn/
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18776790
The website of Zhangpu county in southern Fujian of China
en.zhangpu.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18778811
The website of Jiamusi Environmental Emergency Command Center
hjzx.jms.gov.cn/
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18778901
The website of Henan Province Industry and SME Service Bureau of Information Technology
zxqylm.smehen.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18778920
The website of Jiawang urban shantytowns headquarters
cgb.xzjw.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18776079
The website of Tangxia Town School
hlcz.jmpj.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18776633
The website of Delingha Civil Air Defense
dlhrfb.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18779472
The website of Jinzhong City Softball Association
roliball.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18779407
The website of Yima City East Regional Office
ymdq.gov.cn
http://www.zone-h.org/mirror/id/18778949
This website is unknown to me
http://www.bcjw.gov.cn/
http://www.zone-h.org/mirror/id/18778759
The website of Ziyang Government Yanjiang Baotai
btzf.gov.cn
Mirror of hacked website
http://www.zone-h.org/mirror/id/18778752
The website of Quanjiao Tourism Sports Association:
qjwtj.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18778750
The website of Red Dragon home improvement network
hljtf.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18778681
The website of Environmental Network group
hljepb.gov.cn
http://www.zone-h.org/mirror/id/18776870
An other unknown Chinese government website
jchd.gov.cn
Mirror of the hacked website:
http://www.zone-h.org/mirror/id/18776818
The website of Business Corporation group
hbwnmc.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18776808
An other unknown hacked site
dpfpymj.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18776706
The website of Bureau of Justice Yandu County:
ydsfj.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18776162
The website of Intellectual property office of Zhaotong City, Yunnan Provence Science and Technology Bureau
ztst.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18776098
The website of Jianshi County, Organization Department
jsdjw.gov.cn
Mirror of hacked website:
http://www.zone-h.org/mirror/id/18775047
To view all the hacks done by Barbaros-DZ Algerian hacker on China, click here
At the time of publishing this article, some of the sites were restored while some of the sites were taken offline.

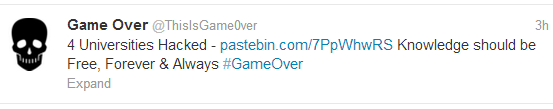

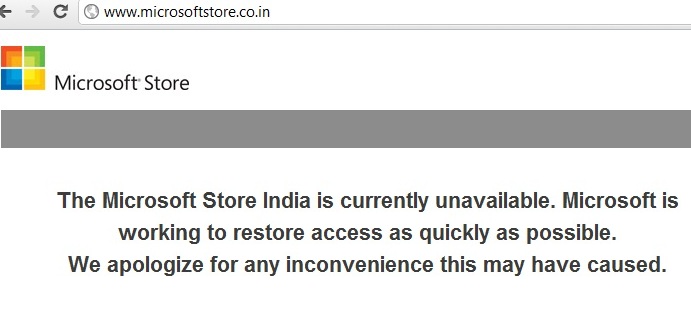
 Where Anonymous declared war on the Israeli websites , today another Pakistani hacking group also came forward in support of GAZA by taking down multiple big Israeli sites and deface all Microsoft related Israeli domains including Bing, MSN, Skype, Live and other.
Where Anonymous declared war on the Israeli websites , today another Pakistani hacking group also came forward in support of GAZA by taking down multiple big Israeli sites and deface all Microsoft related Israeli domains including Bing, MSN, Skype, Live and other.

![Download Cricket Power-Play Game for all iOS [Download Link Available] Download Cricket Power-Play Game for all iOS [Download Link Available]](http://hackread.com/wp-content/themes/goodnews4/framework/scripts/timthumb.php?src=http://hackread.com/wp-content/uploads/2012/12/Cricket-Power-Play-downloads-300x168.jpg&h=193&w=215&zc=1)

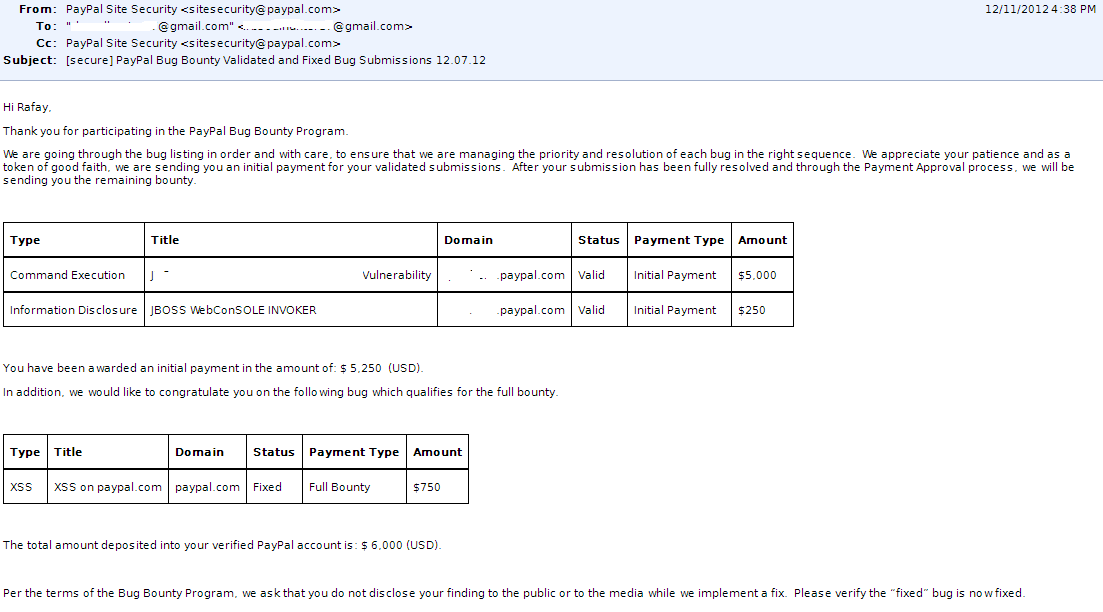







 A Cross Site Request Forgery(CSRF) vulnerability in Facebook allowed hackers to record video of target users and post in the victim's wall. The vulnerability was discovered by security researchers Aditya Gupta and Subho Halder, from XYSEC Team .
A Cross Site Request Forgery(CSRF) vulnerability in Facebook allowed hackers to record video of target users and post in the victim's wall. The vulnerability was discovered by security researchers Aditya Gupta and Subho Halder, from XYSEC Team . Hackers once again breached the Point-of-Sale(POS) network of Restaurant Depot, New York based wholesale supplier. The hackers managed to steal credit and debit card details from the card processing system they use in some of their stores.
Hackers once again breached the Point-of-Sale(POS) network of Restaurant Depot, New York based wholesale supplier. The hackers managed to steal credit and debit card details from the card processing system they use in some of their stores. Do you have any idea about an Internal IP Address or a Private IP Address that too assigned for Multinational Companies? Yeah, today we are gonna discuss about Internal IP or Private IP address Disclosure.
Do you have any idea about an Internal IP Address or a Private IP Address that too assigned for Multinational Companies? Yeah, today we are gonna discuss about Internal IP or Private IP address Disclosure.



 Card-not-present transactions present merchants with fraud prevention challenges that are either non-existent or much easier to address in a card-present environment. E-commerce merchants are required to verify the validity of all bank cards submitted for payment on their websites, just as their brick-and-mortar counterparts are required to do in their physical stores.
Card-not-present transactions present merchants with fraud prevention challenges that are either non-existent or much easier to address in a card-present environment. E-commerce merchants are required to verify the validity of all bank cards submitted for payment on their websites, just as their brick-and-mortar counterparts are required to do in their physical stores.